[Updated 2012-01-29. Thank you to my net pal Al for editing corrections and inspiring me to document the difference between old Mozilla browsers and new.]
Is there a smiley for rolling one's eyes? Maybe this will do: (@_@)
Stupid, lazy, incompetent Oracle:
MAKE JAVA OPEN SOURCE NOW NOW NOW!
The open source community couldn't do any worse than Oracle's worthless support for Java.
Go and read this NOW:
Java’s new “very high” security mode can't protect you from malware
by Dan Goodin - Jan 28 2013, 1:55pm EST
Security researchers have uncovered a newly discovered bug in Oracle's Java framework that allows attackers to bypass important security protections designed to prevent malware attacks. . .
The security bypass was only tested on Windows. But expect it to be fully functional on Mac Java as well.
Oracle representatives didn't immediately respond to an e-mail seeking comment for this post. In addition to shoring up the quality of the Java code base, many security professionals have called on Oracle to communicate more quickly and effectively when it learns of new vulnerabilities in recent versions of its software.
What a concept: Oracle caring and reacting effectively in a timely manner. We can dream.
Just Turn Java Off
That means turn Java OFF, and leave it off, in ALL your web browsers until you have ALREADY loaded a website where you require Java. At that point you can reload the web page for full Java plugin functionality. Then remember to turn Java OFF again BEFORE you leave that website.
Other ways to Just Turn Java Off :
A) Quit all your web browsers.
B) Go here: /Library/Internet Plug-ins/
C) Find 'JavaAppletPlugin.plugin' AND 'JavaEmbeddingPlugin.bundle' (if present).
D) Toss them somewhere else to disable them from loading into your web browsers. This will require an Administrator password. (Be certain you've actually MOVED the plugin files, not simply copied them!) I keep the Java files in a folder inside /Library I have named 'Internet Plug-Ins (Disabled)'. I can move them back into /Library/Internet Plug-ins/ whenever I like in order to restore functionality.
E) At that point you can boot your web browsers and damnable Java can't load, so you're safe.
The PERMANENT method for removing Java (except for Firefox) is to:
Go here and follow Oracle's instructions:
Or, if you would like more complete instructions, there is one added file you can remove at your discretion:
A - D) As above. Except toss the Java files into your Trash and empty it, as found in Oracle's instructions.
E) Go here: /Library/PreferencePanes/
F) Find the alias file labeled 'JavaControlPanel.prefpane' and trash it. It's left over refuse of no worth to anyone.
Stop there. You're done.
Yes, there are other Java files on your Mac, but they are from Apple. Don't touch them. This includes the 'Java' folder inside /Library and the other files aliased from that folder. Apple and other apps use Java within your Mac's operating system. (Java isn't just for the Internet), None of these apps and services are affected by Oracle and their continuing circus of blundering and carelessness. You're safe.
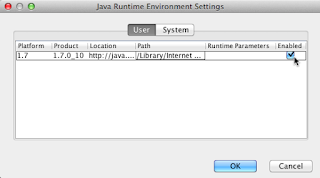
BTW: I still cannot turn Java off via the 'checkbox' provided in Oracle's 'Control Panel' for 7u11. It is permanently ON. I've tested it on 10.7.5, 10.8.2 and the 10.8.3 beta. It's broken under both the 'User' tab and the 'System' tab. Oracle know it. Their workaround for 10.8.2 FAILed for me. Therefore, the only solution is to turn Java off in all your web browsers or simply remove the plugin from your /Library/Internet Plug-ins/ folder and restart your web browsers.
IASSOTS
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
ADDENDUM
Firefox and other Mozilla related apps:
BTW: I still cannot turn Java off via the 'checkbox' provided in Oracle's 'Control Panel' for 7u11. It is permanently ON. I've tested it on 10.7.5, 10.8.2 and the 10.8.3 beta. It's broken under both the 'User' tab and the 'System' tab. Oracle know it. Their workaround for 10.8.2 FAILed for me. Therefore, the only solution is to turn Java off in all your web browsers or simply remove the plugin from your /Library/Internet Plug-ins/ folder and restart your web browsers.
IASSOTS
Stupid, lazy, incompetent Oracle. (0_o)
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
ADDENDUM
Firefox and other Mozilla related apps:
Summary: All of the above instructions still apply, as long as you are using the most current version of Firefox.
However, some people still use older versions of Mozilla apps AND Firefox still links to old, wrong, out-of-date instructions for updating Java. Therefore, I've added this addendum to help prevent confusion:
Old (less secure) versions of Mozilla applications embedded Java plugins within the applications themselves. Updates were required from the SourceForge.net website.
Current and recent versions of Mozilla applications now access the same Java plugin installed into OS X via the Oracle Java installer. IOW: There is no longer any separate version of the Java plugin used by Mozilla apps.
You can access Mozilla's current Java instructions here:
Remaining Confusion: Unfortunately, if you go into the current version of Firefox (v18.0.1), check the Add-Ons Manager and open the Plugins tab, you'll find WRONG instructions (linked to 'Check to see if your plugins are up to date') for updating the Java Embedding Plugin. Firefox v18.0.1 says it includes Java Embedding Plugin v1.0-JEP-0.9.7.3 while the most recent version at SourceForge is v0.9.7.5. Ignore this. There is no actual way to update to v0.9.7.5 AND it doesn't matter. Instead, follow Mozilla's instructions linked above. That is all.
Just make certain that Firefox's Java Embedding Plugin is 'disabled' in Add-Ons Manager. You can 'enable' it again when you want to use Java on a specific website. Disable it again before you leave that website, the same as usual.
--