--
When I was a computer newbie, what I heard repeatedly was "The Number One Rule Of Computing is Make A Backup!" I've been working on an extended list beyond one item in order to help newer newbies consider further aspects of their computer experience that can help save them in a crisis. I don't consider my list definitive or even finished. But I like the list enough to publish it as a starting guide. So here I go:
The Rules Of Computing
1) Make a backup. Have two backup strategies. One strategy regularly backs up your crucial data to local external media away from your computer. The other strategy backup up this same data to an off-site location, such as in 'the cloud' or onto external media you take to a separate location each day. The idea is to have an off-site backup in case your computer site burns to the ground. Backups are also your first and best defense against malware damage and hardware failures. If you don't back up your data, you get what you deserve.
2) Verify all software before installing it. Verify your software source is reliable and that the software itself is reliable. Look up the software title on the Internet using a search engine to discover if it has been reported as problematic. Download software from reliable sources such as VersionTracker, MacUpdate, Major Geeks, etc. Don’t ever blindly install emailed software. It could be malware.
3) Verify that websites you visit are legitimate. This third rule is difficult to implement on your own. Use tools provided inside web browsers, as well as add-on browser extensions, that help you check websites you visit against a blacklist of known bad websites. One of the most popular ways of spreading malware at this time is via 'drive-by' infections via JavaScript and Java. Don't ever blindly click on web links in email. The could be sending you to a malware infection or identity phishing website.
4) Keep your computer up-to-date with the most recent security updates. Apple provide security updates on a regular basis. Security Preferences, built into Mac OS X, should let you know when an update is available. You can also open Security Preferences yourself and have it check for you.
5) Use a 'Standard' account when surfing the Internet or using your Mac on any network. Do NOT use an 'Administrator' account in these situations. This is not a cure all to prevent your Mac from becoming hacked or malware infected. But it adds a terrific layer of security to help prevent malicious root access to your computer.
6) Password protect your user account. Make sure your account password is not a dictionary word or you'll be hacked in no time flat. Use something long and obscure that you can remember but that you expect no one could guess. To this day I run into people who tell me 'But I'm the only one who uses my computer!'. Cure your ignorance please. There is NO excuse for not protecting your computer with a password. If you don't protect your user account, you get what you deserve.
Yes, I'm that mean and cruel when it comes to computer security. There are wonderful security strategies and tools that Apple provide, such as Time Machine, Disk Utility, Standard user accounts and password protection. If you don't put them to use, I have no sympathy! If you have questions about how to make them work for you, write to me, talk to Mac users you know, contact users on the Internet or at your local Mac user group. These tools are not difficult. They are important and they are FREE.
A Few Further Strategies:
I'm only going to list these strategies as they are more complicated and involved to install and get running. What's important is that they are available, they are also FREE, and they may well save you from giving away data to the bad guys.
A) FileVault. You will find it inside the Security System Preferences. It lets you transparently encrypt your entire user account folder so no one can ever get to your data without knowing the decryption password. This is rock solid encryption you can rely upon. Apple will be providing an option for encrypting your ENTIRE computer hard drive in Mac OS X 10.7 Lion. I personally consider whold drive encryption to be overkill. But it is considered to be critical in Enterprise business situations. Note that there are some minor dysfunctions that result from encrypting your user account. But if you have critical data, it is an excellent security tool.
B) Firmware Password. Apple provide a utility to set their Firmware Password Utility on all Mac OS X installation DVDs. It adds another layer of security to keep the bad guys out of your computer. Sadly, it is not fool proof. A tech savvy bad guy can work around it. Encryption is a much more effective tool. Also note that you lose some minor computer functionality when you use a firmware password.
C) GnuPG, aka GNU Privacy Guard. I have been using GPG for many years at this point. I'm a fairly infamous critic of the bugs that have should up in the related tools from time to time. Also note that GnuPG has a steep learning curve and can be a bit frustrating. However, it is a FREE and brilliant tool with many users. You can encrypt and password protect anything you like. The Apple Mail tool lets you digitally sign all your email in order to verify exactly who you are to those who receive your email. You can encrypt your email such that no one can read it in transit over the Internet. It lets you create any number of encryption keys as well as collect public keys from your friends and acquaintances. And more! If you want to be serious about encryption, GPG is excellent. These days it also has a terrific group of developers dedicated to keeping it bug free and up-to-date.
D) Disk Utility. Among the many features of the Mac OS X Disk Utility application is the ability to create encrypted, password protected .sparseimage files. I absolutely love this feature and use a sparseimage I created all day, every day. I have my sparseimage open every time I log into my user account. I provide the decryption password and it sits on my desktop like a disk volume. Anything I put into it is encrypted and unavailable to anyone but me as soon as I close the disk image. Because its a sparseimage, it can grow to as large a size as you choose as you add more into it. Recently the DropBox application and server have become notorious because nothing-at-all is encrypted when you use it. That can be very bad. However, I work around this problem by putting only my sparseimage file into my drop box. No one has any access to anything I have in my DropBox ever, thanks to this great tool.
E) Anti-Malware applications. I own, use and love Intego's VirusBarrier X6 ($50). There aren't any better anti-malware applications, period. But I have to pay for malware signatures every year. If you are a professional user, VirusBarrier is well worth the cost.
If you're a casual computer user, paying for anti-malware is a bit less critical. I've worked fairly closely with Mark Allan and friends who develop and support the FREE program ClamXav. There was a time when I had quite the run-in with the ClamAV Open Source project because most volunteers there cared not-a-whit about Mac OS X. But gradually Mark and I managed to turn a few heads and encourage them to get up-to-date with current Mac malware. At this point in time I can tell you that just about all current Mac malware is being detected by ClamAV. Therefore, I highly recommend downloading, installing and running ClamXav from time to time if you are concerned about malware. The GUI Mark provides is excellent.
Also, if you own Snow Leopard Cache Cleaner ($15) you will find that it includes its own implementation of ClamAV, also highly recommended. I no longer recommend free iAntiVirus as it is now out-of-date and less effective than the ClamAV alternatives.
There are plenty more security tools and strategies, both free and for a fee. But the above is a good start with reasonable coverage.
For the extra security conscious, as ever I highly recommend the TWiT.tv podcast 'Security Now' with the most excellent Steve Gibson. It gets highly technical but is wonderfully presented and very contemporary. You can look up the podcast in iTunes or visit its dedicated webpage at:
http://GRC.com/SecurityNow
:-Derek
--
Thursday, May 19, 2011
US NSA (National Security Agency):
'Hardening Tips for Mac OS X 10.6 Snow Leopard'
I believe I mentioned this publication last year. I was reminded of it by a tweet from Dr. Charlie Miller today:
NSA's hardening tips for OS X 10.6 < looks like a good way to make things randomly stop working.Oh dear. But the brochure has helped me today to finish up my current 6 Rules Of Computing list, which I will post as my next article.
Overall, the NSA's 'tips' are fine and useful. But they go a bit mental over trivial points. Some examples:
A) Their section entitled: "Au Revoir, Bonjour!" is TechTardy from my POV. They suggest using a Terminal command to turn Bonjour off. Ignore it. Bonjour is an innovation I personally love. It has nothing (so far) to do with compromising a Mac's security.
B) Their section entitled "Disable Bluetooth and AirPort Devices" is whacked. I'm all for killing off Bluetooth technology, which I despise as decrepit, low bandwidth, buggy and insecure. But to have the NSA say you need a "certified technician" to remove your Bluetooth hardware is absurd. Equally, their suggestions about disabling AirPort are strange and likely to lead to unnecessary confusion.
C) Their redundant "Disable IPv6 and AirPort when Not Needed" section continues the strange and confusing. There is no reason to disable IPv6 at all. In fact, a year from now we are all going to find IPv6 to be essential when surfing the web.
Etcetera.
The weak points in the brochure continue to dismay my trust in US government comprehension of contemporary technology. I've railed against NSA technology ignorance before and at this rate I expect I'll be railing on them for years to come.
--
FUD! FUD! FUD! FUD!
Anti-Apple Security FUD
for the last SEVEN and a half years!
Hee hee hee!
So what does computer security FUD actually signify? Insecurity on the part of those who perpetrate it.
If you haven't read it already, here is a wonderfully insulting article about the ongoing anti-Apple security FUD Fest. It is from John Gruber of DaringFireball.net:
Hey, I learned something new! It was NOT Symantec who kicked off the FUD Fest in March 2005! It was Eric Hellweg, October 2004, in an article entitled "Hackers Target Apple? Congratulations!"
Let's stroll down nostalgia lane and read some of what Mr. Hellweg perpetrated:
Here is what I consider to be the definitive publication on the subject:
The World's safest Operating System
(One example: The Canonical Display Driver security bug in 64-bit Windows 7, May 2010).
Let's perform a brief Compare and Contrast exercise:
New Mac OS X malware this past week, as reported by Sophos:
• OSX/FakeAV-DPU: 4 variations of a scamware anti-malware Trojan horse (MAC Defender, MacSecurity, MacProtector...).
New Windows malware on May 10th, as reported by Sophos:
• Troj/Hiloti-BZ
• Troj/FakeAV-DPV
• Troj/Avent-RNY
• Troj/DwnLdr-JAZ
• Troj/SpyEye-AJ
• Troj/Agent-RNZ
• Troj/FakeAV-DPT
• Troj/JavaDI-CF
• TrojDwnLDR-JAY
New Windows malware May 11th, as reported by Sophos:
• Troj/Mdrop-DKE
• Troj/Sasfis-O
• Troj/Zbot-AOY
• Troj/Zbot-AOW
• W32/Womble-E
• Troj/VB-FGD
• Troj/FakeAV-DFF
• Troj/SWFLdr-W
• W32/RorpiaMem-A
• Troj/Agent-RNT
• Troj/DwnLdr-JAE
• Troj/FakeAV-DPS
Get the idea? That's about 70 new malware per week for Windows compared to 1 new malware per week for Mac OS X, and that's a heavy week for Mac malware. That's a rough ratio of 70 : 1. Keep in mind that the current ratio of Windows market share to Mac market share is about 87% : 10% or about 8.7 : 1. Note how the malware ratio is not tracking the market share ratio.
What if we compare the total number of currently active Windows malware to the current number of active Mac OS X malware?
Finding any published number appears to be impossible. I have what I consider a definitive number of currently active Mac OS X malware because I collect data on all of them as they appear in the wild. That number is 30, as of today anyway. That generously includes four variations of the scamware anti-malware app originally called MAC Defender.
To come up with a number for Windows malware, I had to do a bit of work. First I went to Symantec's Threat Explorer and collected the numbers they provided from A-Z. I then subtracted the number of Mac OS X malware in their list. That total of Windows malware detected by Symantec, as of today, is 39,335. Why this number is so small compared to other estimates is up to Symantec. I don't mind!
39,335 : 30 = 1311.17 : 1
That's about 1311 x more malware for Windows than for Mac OS X.
Using our market share ratio of 8.7 : 1, let's create a proportion equasion of malware on a per user basis. This means, if the number of users of both operating systems was equal, how many more malware are there for Windows than for Mac OS X?
1311 / 1 = (8.7 / 1) * X
X = 150.69 per user
That means, on a per user basis, there are about 150 times more malware for Windows.
150x ! ! !
Meanwhile, here is a reiteration of my often stated complaint against Apple's worst security flaw:
Seriously! What is your problem Apple?! You're going to stick us with 32-bit QuickTime 7 again in Mac OS X 10.7 Lion? In a fully 64-bit operating system? Disgraceful.
If you haven't read it already, here is a wonderfully insulting article about the ongoing anti-Apple security FUD Fest. It is from John Gruber of DaringFireball.net:
Hey, I learned something new! It was NOT Symantec who kicked off the FUD Fest in March 2005! It was Eric Hellweg, October 2004, in an article entitled "Hackers Target Apple? Congratulations!"
Let's stroll down nostalgia lane and read some of what Mr. Hellweg perpetrated:
The Apple community has, since its inception, been largely immune to nefarious hackers bent on spreading harm. If you are a Windows user, as I am, you know the routine. You complain about the latest spyware or virus attack, and Apple devotees respond with good-natured teasing — they don’t have worry about such nonsense. Well, now they do.
Predictably, posts on various Apple-related message boards have been offering varying levels of concern, ranging from mild disappointment to utter gloom. I think this reaction is fundamentally misguided. MAC users should not be upset about this malware news; they should rejoice.
What is really going on here? It's called Defective Rationalization, Deceptive 'Truth', or more popularly, the act of being an Apologist. From WordNet:
apologist
n : a person who argues to defend or justify some policy or institution; "an apologist for capital punishment" [syn: vindicator, justifier]What is being 'justified' or 'vindicated' by all the anti-Apple security FUD, hate, cynicism and doom mongering?
Windows
Here is what I consider to be the definitive publication on the subject:
The World's safest Operating System
London, UK - 19 February 2004, 17:30 GMT - A study by the mi2g Intelligence Unit reveals that the world's safest and most secure online server Operating System (OS) is proving to be the Open Source family of BSD (Berkley Software Distribution) and the Mac OS X based on Darwin. The study also reveals that Linux has become the most breached online server OS in the government and non-government spheres for the first time, while the number of successful hacker attacks against Microsoft Windows based servers have fallen consistently for the last ten months.That was in 2004. Since that time, to be fair, Microsoft got more serious about security with Windows Vista. They refined their security features in Windows 7ista. These two operating systems have been significantly more secure thanks to features like ASLR (Address Space Layout Randomization) and DEP (Data Execution Prevention). These are security features that Apple has yet to perfect in Mac OS X. And yet, even Windows 7 has enough security holes to keep the the Windows operating system on the bottom of the OS security list.
(One example: The Canonical Display Driver security bug in 64-bit Windows 7, May 2010).
Let's perform a brief Compare and Contrast exercise:
New Mac OS X malware this past week, as reported by Sophos:
• OSX/FakeAV-DPU: 4 variations of a scamware anti-malware Trojan horse (MAC Defender, MacSecurity, MacProtector...).
New Windows malware on May 10th, as reported by Sophos:
• Troj/Hiloti-BZ
• Troj/FakeAV-DPV
• Troj/Avent-RNY
• Troj/DwnLdr-JAZ
• Troj/SpyEye-AJ
• Troj/Agent-RNZ
• Troj/FakeAV-DPT
• Troj/JavaDI-CF
• TrojDwnLDR-JAY
New Windows malware May 11th, as reported by Sophos:
• Troj/Mdrop-DKE
• Troj/Sasfis-O
• Troj/Zbot-AOY
• Troj/Zbot-AOW
• W32/Womble-E
• Troj/VB-FGD
• Troj/FakeAV-DFF
• Troj/SWFLdr-W
• W32/RorpiaMem-A
• Troj/Agent-RNT
• Troj/DwnLdr-JAE
• Troj/FakeAV-DPS
Get the idea? That's about 70 new malware per week for Windows compared to 1 new malware per week for Mac OS X, and that's a heavy week for Mac malware. That's a rough ratio of 70 : 1. Keep in mind that the current ratio of Windows market share to Mac market share is about 87% : 10% or about 8.7 : 1. Note how the malware ratio is not tracking the market share ratio.
What if we compare the total number of currently active Windows malware to the current number of active Mac OS X malware?
Finding any published number appears to be impossible. I have what I consider a definitive number of currently active Mac OS X malware because I collect data on all of them as they appear in the wild. That number is 30, as of today anyway. That generously includes four variations of the scamware anti-malware app originally called MAC Defender.
To come up with a number for Windows malware, I had to do a bit of work. First I went to Symantec's Threat Explorer and collected the numbers they provided from A-Z. I then subtracted the number of Mac OS X malware in their list. That total of Windows malware detected by Symantec, as of today, is 39,335. Why this number is so small compared to other estimates is up to Symantec. I don't mind!
39,335 : 30 = 1311.17 : 1
That's about 1311 x more malware for Windows than for Mac OS X.
Using our market share ratio of 8.7 : 1, let's create a proportion equasion of malware on a per user basis. This means, if the number of users of both operating systems was equal, how many more malware are there for Windows than for Mac OS X?
1311 / 1 = (8.7 / 1) * X
X = 150.69 per user
That means, on a per user basis, there are about 150 times more malware for Windows.
150x ! ! !
And this does not equate to poorer Windows security because why?
Oh and so much for the 'Security Through Obscurity' baloney. What's obscure is the number of Mac malware as well as the intelligence of STO proponents.
FACT: There is no such thing as a perfect operating system. Mac OS X has security holes discovered and patched on a regular basis.
Oh and so much for the 'Security Through Obscurity' baloney. What's obscure is the number of Mac malware as well as the intelligence of STO proponents.
FACT: There is no such thing as a perfect operating system. Mac OS X has security holes discovered and patched on a regular basis.
FACT: Since I noticed the start of the anti-Apple security FUD Fest in 2005, Apple have exponentially increased their attention to security. I like that. Thank you FUDsters and hackers!!!
FACT: I've never encountered a Mac OS X malware infection. I run an up-to-date copy of Intego Virus Barrier X6 to verify this fact. I have also run VirusBarrier X6 against a collection of malware provided to me by friends. It works.
FACT: Nearly all Mac OS X malware requires social engineering / LUSER behavior in order to be installed on a Mac. There are no viruses or worms for Mac OS X. There are no malware that exploits any Mac OS X security hole.
FACT: The vast majority of hacks and cracks into Mac OS X have been either through 3rd party software, such as Flash, PDFs and JavaScript, or through Apple's Achilles Heel of insecurity: QuickTime.
If you're a Windows apologist and would like to dispute my numbers or information, please post a comment. (Troll posts will be tossed).
FACT: The vast majority of hacks and cracks into Mac OS X have been either through 3rd party software, such as Flash, PDFs and JavaScript, or through Apple's Achilles Heel of insecurity: QuickTime.
If you're a Windows apologist and would like to dispute my numbers or information, please post a comment. (Troll posts will be tossed).
Meanwhile, here is a reiteration of my often stated complaint against Apple's worst security flaw:
HEY APPLE!
Why didn't you finish the 64-bit rewrite of QuickTime X LAST YEAR?!?!?!
Where the H E L L is it?!
Tuesday, May 10, 2011
Removing Scamware:
Generic Instructions
With the ongoing FAKE anti-virus scamware (rogueware/scareware) rat attack, I thought it would be useful to provide a generic set of instructions for removing these annoying and illegal programs. Clearly the rats perpetrating this garbage are persistent. As of May 8th there are three versions of this scam. Therefore, keeping these instructions generic is all the more useful. If you have any questions, please comment below and I'll do my best to update these instructions to provide better clarity.
BTW: Thanks to the folks at MacScan for getting the ball rolling with their instructions for removing the MAC Defender scamware.
How To Remove Scamware (v1.0.0):
Introduction: There are three concerns when removing scamware. The first is stopping the currently running scamware process. The second is removing the application. The third is removing any reference to application in your startup process files. You will see these three concerns addressed below. (Note that this removal procedure does NOT apply to rootkit infections, which require a more complicated removal procedure).
Stomping Steps:
1) Note the name of the scamware (rogueware) you have inadvertently installed.
2) Run the Activity Monitor program, located in your Applications/Utilities folder. Be certain that the pop-up menu at the top of the app's window is set to "All Processes".
3) Filter or scan down the list of active processes for the name of the scamware. In the case of "MAC Defender", the process is named 'MacDefender'. Similar process names most likely will apply to other scamware. (Note: It is easier to scan the list of processes if you click the "Process Name" column header in order to sort the process names alphabetically).
4) Click on the name of the scamware process to highlight it.
5) At the top left of the app window, click on the "Quit Process" button. It looks like a red stop sign.
6) In the resulting drop-down box, click on "Force Quit". That stops the scamware process from running in your computer, for the moment. You can Quit Activity Monitor at this point.
7) Navigate using the Finder to the Applications folder. It is likely that somewhere in this folder will be the application file for the scamware. Either Search for it or scan down the list of applications (including inside the Utilities folder) to find it.
8) Click on the name of the scamware. Drag it to your Trash. Empty your trash. (Note that if you attempt to empty the trash while the scamware is still running, the system will stop you. Quit the scamware process first via Activity Monitor).
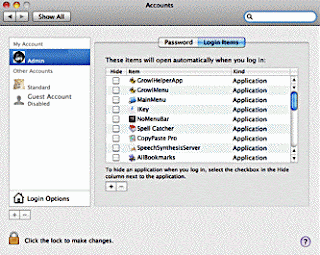
9) Remove any reference to the scamware from your startup process list: You can do this by opening your System Preferences the opening the 'Accounts' preferences pane. Along the top of the pane you will see two tab buttons. Click on 'Login Items'.
10) Scan down the list of Login Items until you see the name of the scamware. Click on the name to highlight it.
11) Click on the minus sign (-) below the list in order to remove the scamware from your Login Items. You're done.
That may be all you need to do to get rid of the thing. There are other ways for malware in general to infect themselves into your system. If further search and navigation methods are required to remove further traces of the scamware, I will add them to the instructions above and progress the version number of these instructions another iteration.
Hope that helps!
:-Derek
BTW: Thanks to the folks at MacScan for getting the ball rolling with their instructions for removing the MAC Defender scamware.
How To Remove Scamware (v1.0.0):
Introduction: There are three concerns when removing scamware. The first is stopping the currently running scamware process. The second is removing the application. The third is removing any reference to application in your startup process files. You will see these three concerns addressed below. (Note that this removal procedure does NOT apply to rootkit infections, which require a more complicated removal procedure).
Stomping Steps:
1) Note the name of the scamware (rogueware) you have inadvertently installed.
2) Run the Activity Monitor program, located in your Applications/Utilities folder. Be certain that the pop-up menu at the top of the app's window is set to "All Processes".
3) Filter or scan down the list of active processes for the name of the scamware. In the case of "MAC Defender", the process is named 'MacDefender'. Similar process names most likely will apply to other scamware. (Note: It is easier to scan the list of processes if you click the "Process Name" column header in order to sort the process names alphabetically).
4) Click on the name of the scamware process to highlight it.
5) At the top left of the app window, click on the "Quit Process" button. It looks like a red stop sign.
6) In the resulting drop-down box, click on "Force Quit". That stops the scamware process from running in your computer, for the moment. You can Quit Activity Monitor at this point.
7) Navigate using the Finder to the Applications folder. It is likely that somewhere in this folder will be the application file for the scamware. Either Search for it or scan down the list of applications (including inside the Utilities folder) to find it.
8) Click on the name of the scamware. Drag it to your Trash. Empty your trash. (Note that if you attempt to empty the trash while the scamware is still running, the system will stop you. Quit the scamware process first via Activity Monitor).
9) Remove any reference to the scamware from your startup process list: You can do this by opening your System Preferences the opening the 'Accounts' preferences pane. Along the top of the pane you will see two tab buttons. Click on 'Login Items'.
10) Scan down the list of Login Items until you see the name of the scamware. Click on the name to highlight it.
11) Click on the minus sign (-) below the list in order to remove the scamware from your Login Items. You're done.
That may be all you need to do to get rid of the thing. There are other ways for malware in general to infect themselves into your system. If further search and navigation methods are required to remove further traces of the scamware, I will add them to the instructions above and progress the version number of these instructions another iteration.
Hope that helps!
:-Derek
Thursday, May 5, 2011
"Mac Security" Scamware:
Variations on a Fake
How I love the hunt!
Today's prey is an Internet rat known as species 'Scamware stupidicus'.
The rats who brought you the scamware (rogueware) "MAC Defender" (see my previous blog post) have now tweaked their code slightly and renamed the thing "Mac Security" with an installer entitled "BestMacAntivirus2011.mpkg.zip" which expands to the installer file "MacSecurity.mpkg". Expect there to be other name variations.
Good old Intego discovered this new variation, posting an article and a "How It Works" video here:
Intego Discovers New Variants of Mac Defender Fake Antivirus
You can directly watch the video on YouTube HERE.
Intego have updated their Virus Barrier malware signatures to detect this new rodent excrement.
What is hilarious about this scamware is the LAZINESS of the hacker rats who wrote it. The interface for the scamware is that of Microsoft WINDOWS!!! Hardy har. If you've used Windows in the last decade, you'll spot it immediately as BOGUS.
At this time the dangers are:
A) You fork out $money$ to buy useless garbage.
B) You give away your CREDIT CARD to criminals. It's a good as posting your card publicly on the Internet.
C) You give away your computer's PASSWORD. (This is now clearly evident from Intego's provided video). Consider yourself as good as PWNed (i.e. botted, i.e. zombied, i.e. no longer in control of your computer). So far the Trojan horse software is 'empty', containing nothing dangerous. But it could! Most likely, future variations will.
As with all current Mac malware, this POS relies upon social engineering, aka LUSER behavior, to entice the user to install it. Don't do that!
To keep ourselves safe, let's chant the mantra of...
The Top Two Rules Of Computing:
I) Make A Backup.
II) Verify All Software Before Installing It Or Running It.
(I'm considering using the following as Rule III:
III) Verify all links before clicking them).
Happy shooting!
--
Today's prey is an Internet rat known as species 'Scamware stupidicus'.
The rats who brought you the scamware (rogueware) "MAC Defender" (see my previous blog post) have now tweaked their code slightly and renamed the thing "Mac Security" with an installer entitled "BestMacAntivirus2011.mpkg.zip" which expands to the installer file "MacSecurity.mpkg". Expect there to be other name variations.
Good old Intego discovered this new variation, posting an article and a "How It Works" video here:
Intego Discovers New Variants of Mac Defender Fake Antivirus
You can directly watch the video on YouTube HERE.
Intego have updated their Virus Barrier malware signatures to detect this new rodent excrement.
What is hilarious about this scamware is the LAZINESS of the hacker rats who wrote it. The interface for the scamware is that of Microsoft WINDOWS!!! Hardy har. If you've used Windows in the last decade, you'll spot it immediately as BOGUS.
At this time the dangers are:
A) You fork out $money$ to buy useless garbage.
B) You give away your CREDIT CARD to criminals. It's a good as posting your card publicly on the Internet.
C) You give away your computer's PASSWORD. (This is now clearly evident from Intego's provided video). Consider yourself as good as PWNed (i.e. botted, i.e. zombied, i.e. no longer in control of your computer). So far the Trojan horse software is 'empty', containing nothing dangerous. But it could! Most likely, future variations will.
As with all current Mac malware, this POS relies upon social engineering, aka LUSER behavior, to entice the user to install it. Don't do that!
To keep ourselves safe, let's chant the mantra of...
The Top Two Rules Of Computing:
I) Make A Backup.
II) Verify All Software Before Installing It Or Running It.
(I'm considering using the following as Rule III:
III) Verify all links before clicking them).
Happy shooting!
--
Wednesday, May 4, 2011
FAKE "MAC Defender" Scamware Attack
via infected Webpages
What is 'scamware'? (Also known as 'rogueware'). It is a form of malware that pretends to be something it is NOT in order to use social engineering / LUSER behavior to get you to install actual malware. The most numerous kind of scamware occurs on the Internet where you visit a web page and start getting bombarded with messages on your screen that you have been "INFECTED" with whatever, when in fact you have NOT. If you are, let's be blunt, foolish enough to allow your web browser to automatically download software, or even worse, if you allow your web browser to actually OPEN what you automatically download, you're a prime sucker for scamware. Don't do that!
This is the very first instance of actual working scamware for Mac OS X that I am aware of. The most excellent SANS NewsBites Volume 13 Number 35 newsletter issue provides an announcement of the situation as well as resource links. You can sign up for the free SANS newsletters HERE. (I occasionally have disagreements with SANS over their FUD publishing and spelling, but overall they're a terrific resource).
DETAILS
The Scamware: "MAC Defender" (Note the spelling difference from 'MacDefender', which is an actual program developed in Germany, sadly hurt by bad publicity created due to the 'MAC Defender' scamware).
The Infection Vector: Web pages.
The Setup:
1) Through nefarious means, the scamware tosses messages on your screen that you Mac has been infected with something. It insists that you pay $money$ to install the scamware Trojan horse in order to remove the fake 'infection'. Here is an illustration kindly provided by PCWorld.com.
2) If you foolishly allow your web browser to download software, the infected web page will IMMEDIATELY auto-download the Trojan horse to your Mac. THIS IS BAD!
3) If you foolishly allow your web browser to open software it has automatically downloaded, the Trojan horse will automatically open. THIS IS VERY BAD!
4) If you happily never allow auto-anything, then you could still be coerced into clicking the download link for the scamware Trojan horse. Worse yet, you might even open the Trojan horse on your computer. DON'T DO THAT!
At the moment, this scamware attack is occurring at a variety of web pages related to the killing of terrorism scourge Osama Bin Laden. Be extra special watchful at such websites for this scamware.
The STING: You fork over $money$ and your CREDIT CARD information for what is worthless garbage software that does nothing at all. Your credit card has just been stolen.
Note how I still call this scamware a 'Trojan horse'. There are two reasons why. First, it's not what it pretends to be, despite it being an 'empty' Trojan horse. Second, the scamware could easily contain one of the current actual Mac OS X Trojan horses, three of which are capable of botting your Mac. And that's very very bad.
How to Protect Yourself:
A) The Second Rule of Computing! Verify the authenticity and legitimacy of absolutely every piece of software you are tempted to install. In this case, you'll save yourself spending $money$ on worthless garbage as well as your credit card information. Also, seeing as there are currently 28 different Trojan horses for Mac OS X, (26 actually, if you exclude the hacker tools), you'll be preventing yourself from getting infected for real.
Adding to SANS Editor Northcutt's comments in NewsBites, dangerous malware can be hidden in nearly any piece of software. This includes anything you are sent (via email or chat, etc.) or anything at any Internet location.
B) Don't auto anything! That means no auto-download or auto-open. Turn all such features OFF in your web browsers and other Internet related applications. (All such features should be removed from all programs as they are inherently dangerous).
C) Use a decent anti-malware application to protect you from infected web pages. As usual, I recommend Intego VirusBarrier X6, which I own and use and enjoy (usually) and want to marry. When you connect to an potentially dangerous web page, VirusBarrier stops it from loading and warns you of a detected threat. You are able to choose to ignore, block, or add the page to your 'Trusted Sites'.
Here are links with further details for your reading pleasure:
Fake AV Targets Mac OS X Through Poisoned Search Links
Fake "MAC Defender" antivirus app scams users for money, CC numbers
Fake security software takes aim at Mac users
Intego Security Memo – MAC Defender Fake Antivirus Program Targets Mac Users
Fake "MAC Defender" Brings Malware to Macs
Bogus MAC Defender malware campaign targets Mac users using Google Images
Apple Support Communities: Search for 'MACDefender'
(Please note that I corrected the name of this scamware in a few of the the titles above. I see no point in perpetuating misspelling. Thank you as ever to Intego and ars technica for correct spelling ;-).
Subscribe to:
Posts (Atom)