This past week, Apple used their XProtect technology, found in OS X 10.6.8 onwards, to block all versions of Java earlier than 6u51. Here is Apple's security announcement from Thursday:
APPLE-SA-2013-08-29-1 OS X: Java Web plug-in blocked
Due to multiple security issues in older versions, Apple has updated the web plug-in blocking mechanism to disable all versions prior to:
Java 6 update 51
Java 7 update 25
More information on Apple-provided updates is available at
http://support.apple.com/kb/HT5797
Information on blocked web plug-ins will be posted to:
http://support.apple.com/kb/HT5660
OK. Except that's not good enough! According to Information Week, there is NO safe version of Java 6:
Hackers Target Java 6 With Security Exploits
Mathew J. Schwartz | August 26, 2013 11:35 AM | Information Week
Mathew J. Schwartz | August 26, 2013 11:35 AM | Information Week
Warning to anyone still using Java 6: Upgrade now to Java 7 to avoid being compromised by active attacks.
That alert came via F-Secure anti-malware analyst Timo Hirvonen, who reported finding an in-the-wild exploit actively targeting an unpatched vulnerability in Java 6 following the recent publication of related proof-of-concept (POC) attack code. The Java runtime environment (JRE) bug (CVE-2013-2463), was publicly revealed when Oracle released Java 7 update 25 in June 2013, which remains the most recent version of Java. . . .
The safe bet now is to expect no new Java 6 updates. Oracle's Java 6 download page reads: "Updates for Java 6 are no longer available to the public. Oracle offers updates to Java 6 only for customers who have purchased Java support or have Oracle products that require Java 6."
According to statistics released in March 2013, at least 47% of all Java users in the United States were still running Java version 6.
What risk do Java 6 users now face from the new vulnerability that's being exploited? According to vulnerability information provider Secunia, the bug could be "exploited by malicious local users to disclose certain sensitive information, manipulate certain data, and gain escalated privileges and by malicious people to conduct spoofing attacks, disclose certain sensitive information, manipulate certain data, cause a DoS (denial of service), bypass certain security restrictions, and compromise a vulnerable system."
CONCLUSION:
If you are running ANY version of the JavaAppletsPlugin.plugin that is older than version 7u25, TRASH IT! Then restart any web browser you may have open.
Not kidding here folks! You do not want to get PWNed.
Here is where to find your Java plugin on OS X:
/Library/Internet Plug-ins/JavaAppletPlugin.plugin
Check the version number of the plugin via Get Info (⌘-I). If you see anything except "Java 7 Update 25", then doom shall reign upon your computer! You have been warned.
BUT GET THIS!
As per Mathew J. Schwartz' article at Information Week:
While Java 6 is now under the gun, the latest version of Java 7 also sports at least one serious unpatched vulnerability. Fortunately, however, no technical details about that vulnerability have been publicly released. The bug, dubbed "issue 69," was discovered by veteran Java bug hunter Adam Gowdiak, CEO of Polish research firm Security Explorations, and reported to Oracle on July 18, 2013.
IOW: There is already a known security hole in even Java 7 Update 25.
Therefore, even if you MUST use Java on the Web, the very safest thing to do is to:
Just Turn Java OFF.
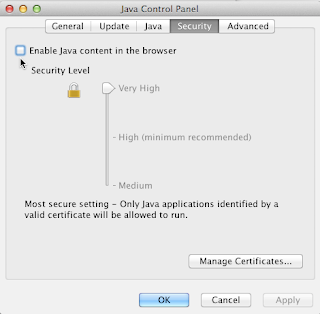
Here is where Oracle now lets you, at long last, turn Java off inside its 'Control Panel' on OS X:
Here's how to get there:
1) Open 'System Preferences...' from the Apple Menu.
2) If you have Java 7 Update 25 installed, you'll see the 'Java' System Preferences button in the bottom 'Other' section of the window. CLICK IT.
3) The 'Java' Preferences pane opens, except it then insists upon running its 'Java Control Panel' in Java as a separate window. (o_0)
4) Click on the 'Security' tab. That will bring up the interface pictured above.
5) If you don't already have the 'Security Level' jammed up to 'Very High', do that FIRST. (You do NOT want it set any lower unless you are at a specifically known safe web page. Of course remember to jam it back UP to 'Very High' again BEFORE you leave that specific web page).
6) Then check OFF the box near the top that is labeled "Enable Java content in the browser". IOW: There should be NO check mark in that box, as seen in the interface pictured above. I have the cursor in the picture pointing at the box.
7) Click the 'Apply' button on the bottom right of the window.
8) Click the OK button. The Java Preferences will close.
What a PITA.
Yes, Apple has very kindly and wisely provided Safari v6.0.5 and higher that automatically stops Java from working on web pages without specific user approval. What a great feature! But I'm providing the instructions above for those who wish to be extra safe. That means you the user take the extra step to make certain no Java malware is going to be able to attack your machine. Consider it paranoia if you will. But this added safety, short of removing the Java plug-in entirely, is available for you to use. It's what I'm using on my Macs.
Meanwhile, when the current known security hole in Java 7u25 begins being exploited in the wild, watch for yet-another Java security update!
Did I mention that I hate you Oracle? :-P
--